Compliance Process
Depending on your internal compliance proesses, we recommend the following controls:- Compliance training: Ensure all authorized Kadoa users complete compliance training and understand your organization’s data sourcing policies.
- Automated compliance checks: Leverage Kadoa’s built-in compliance layer to automatically enforce restrictions.
- Regular reporting and auditing: Assign the compliance officer user role to enable regular auditing across teams.
Automated Compliance Rules
Your compliance team can configure automated checks tailored to your specific organizational requirements. Kadoa supports the following customizable compliance rules:| Rule Type | Description |
|---|---|
| Source Blacklisting | Explicitly prevent extracting or accessing prohibited sources or domains. |
| Captcha & Explicit TOS Enforcement | Prevent automated circumvention of explicit Terms of Service pop-ups and automated Captcha bypassing. |
| Sensitive Data (PII) Detection | Automatically detects attempts to extract common forms of Personally Identifiable Information (PII) and can be configured to redact, flag, or block such data. |
| robots.txt Check | Automatically checks robots.txt directives for all web interactions, promoting ethical data sourcing from websites. |
| Custom Restrictions | Configure fine-grained custom restrictions. |
Compliance Approval Flow
We offer compliance approval functionality for enhanced oversight. When enabled, new workflows require approval from a designated compliance officer during the data preview stage. Compliance officers can approve workflows or reject them with feedback.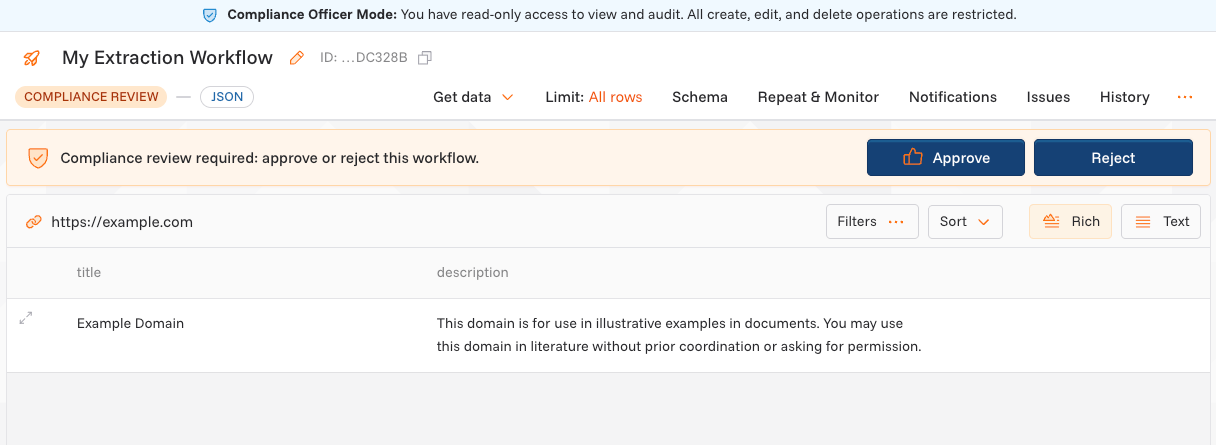
Compliance Center
Compliance officers can access a dedicated compliance center that provides centralized management of compliance rules and reporting features.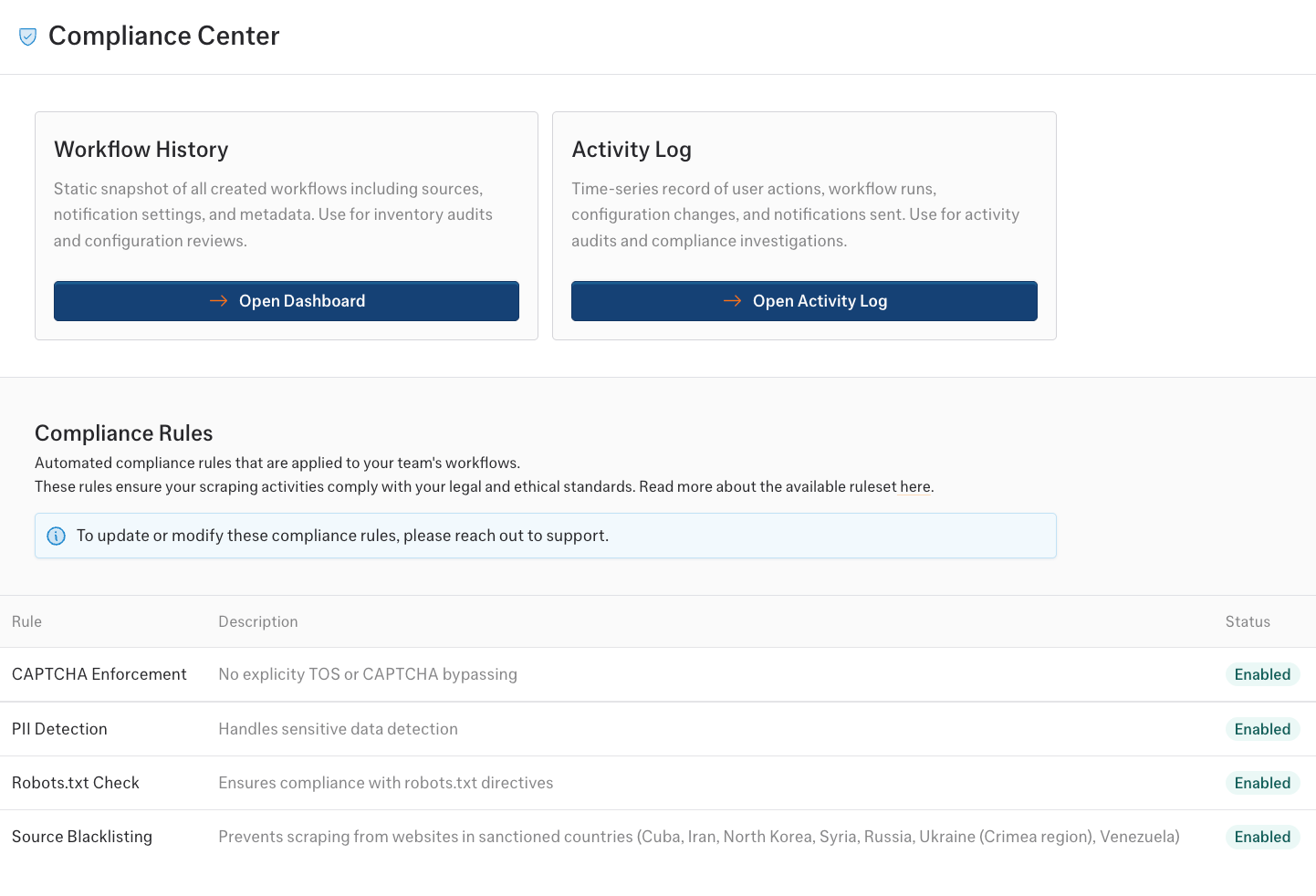
Compliance Rules Management
View and monitor all automated compliance rules configured for your team:- Rule overview: See all active compliance rules and their current status (enabled/disabled)
- Rule descriptions: Clear explanations of what each rule enforces
Reporting
The compliance dashboard includes automated reporting capabilities that allow compliance officers to download comprehensive audit reports:- Workflows History: Complete list of all workflows with details, creation dates, states, and metadata
- Audit Log: All platform interactions are automatically audit logged for complete traceability.
- Data sources accessed or attempted to be accessed.
- Timestamps for workflow runs (start, end, duration).
- User who created, modified, or triggered a workflow/agent.
- Version history and changes made to workflow configurations.
- Number of records or data points extracted.
- Status codes and responses from accessed sources.